Website YPPI - Education ICT in Surabaya
Download soft Jaringan
Download Buku LINUX
Download buku VIRUS
Donwload buku Programing
Download buku seputar jaringan
Download Ost Catatan Akhir Sekolah
Download Lagu Mandarin Full House
About Me

- information technology education
- I'm the man coming from the heroic city of surabaya and of full dedication to the world of education and information Technology in YPPI. I'm still willing to develop and empower my skill & knowedgle so as to step advanced for the nation's future
Blog Theacher SMA YPPI 1
-
ROBOT UNESA BERTANDING DI AMERIKA - Surabaya (beritajatim.com) - Satu lagi kebanggaan yang akan ditunjukan oleh putra-putri terbaik bangsa. Universitas Negeri Surabaya (Unesa) yang dikena...15 tahun yang lalu
-
Mengenali dan membasmi virus koplaz - Virus "K0pL4xZ" yang terdeteksi sebagai VBWorm.QTT mengincar pengguna komputer, khususnya yang memiliki banyak file Office, dengan cara mengganti icon dan ...16 tahun yang lalu
-
MATA PEMIMPIN - ada mata inderawi, ada mata budi, dan ada mata jiwa. Apakah persamaan yang dimiliki oleh tokoh-tokoh sekaliber Sir Winston Churchill, Soekarno, Mohammad Hat...16 tahun yang lalu
-
Resep Masakan Enak Sehari Hari - *Resep Masakan Enak Sehari Hari* http://digestivehealing.com/__media__/js/netsoltrademark.php?d=https://www.dapur-mbu.me/ http://educateboys.com/__media__...3 tahun yang lalu
-
-
gerak air laut - *Gerak Air Laut* Ada 3 gerakan air laut yang akan kita bahas yaitu: arus laut, gelombang laut, dan pasang surut air laut. 1. *Arus Laut* Arus laut (*se...16 tahun yang lalu
-
KEMANDIRIAN DALAM ENTREPRENEUR - Entrepreneurship menjadi kunci keberhasilan sebuah bangsa, meski demikian kondisi bangsa Indonesia belum cukup memiliki entrepreneur yang memadai. Sekol...9 tahun yang lalu
-
Anda Dibentuk untuk Keluarga Allah - Persekutuan berarti terikat satu dng yg lain seperti kita terikat dengan Tuhan.Allah mengharapkan agar kita memberikan hidup kita satu kpd yg lain. Seperti...16 tahun yang lalu
-
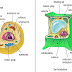
sel hewan dan tumbuhan - *A. Sel (Pendahuluan)* Gbr. Penampang Sel Hewan dan Sel Tumbuhan *Sahabat Amoeba ( Anak muda Biologi **) …,* tahukah kalian bahwa tubuh kita tersusun...16 tahun yang lalu
-
-
ABSTRAKSI PROPOSAL PTK 2007/2008 - PROPOSAL PROGRAM HIBAH PENINGKATAN MUTU PEMBELAJARAN UNIVERSITAS KATOLIK WIDYA MANDALA 2007/2008 PENGGUNAAN METODE PEMBELAJARAN KOOPERATIF MODEL STUDENT TE...16 tahun yang lalu
-
-
-
Mandikan aku Bunda.......... - Cerita ini sangat cocok sebagai bahan renungan bagi kita semua, terutama yang sehari-hari sangat disibukkan dengan aktivitas kerja dan profesi lainnya. Sem...16 tahun yang lalu
-
SEJARAH RENANG - Sejarah Olahraga dan Tehnik - tehnik Olahraga Tehik renang Teknik Rencana utama: Keupayaan berenang Tubuh manusia terdiri sebahagian besarnya daripada air ...10 tahun yang lalu
-
-
-
Honesty - Di jaman sekarang masih adakah orang jujur diketemukan?Mengapa begitu sulitnya menemukan orang jujur di muka bumi ini?Virus apakah yang telah menjangkiti a...15 tahun yang lalu
-
Tenzin Gyatso Zitate / 14TH DALAI LAMA tenzin gyatso INSPIRATIONAL QUOTE POSTER 24X36 kindness | eBay - Para las emociones destructivas, tenemos que ser conscientes de lo que da lugar a ellas y cuáles son los antídotos ~ tenzin gyatso, 14º dalai lama. Tenz...2 tahun yang lalu
-
-
8 kebohongan ibu yang positif - 8 KEBOHONGAN IBU Cerita bermula ketika aku masih kecil, aku terlahir sebagai seorang anak laki-laki di sebuah keluarga yang miskin. Bahkan untuk makan saja...16 tahun yang lalu
-
-
Ciri Orang Cerdas - Bagaimana menurut anda ciri – ciri orang Cerdas ? Apakah dia seorang dengan pendidikan Formal yang tinggi, ataukah Orang tersebut mempunyai pengalaman yang...16 tahun yang lalu
-
OPINI - MENCIPTAKAN SEKOLAH SEBAGAI ZONA NYAMAN BAGI SISWA Bagi siswa, suasana belajar di sekolah sangatlah tidak nyaman, beda dengan dunia luarnya yang dipenuhi d...16 tahun yang lalu
-
-
Pembelajaran Interaktif - *Pembelajaran Interaktif Merupakan Suatu Kebutuhan* *Theresia Henywati – Kepala SMA YPPI - I* Memasuki era global , pada tahun pelajaran 2008 / 2009 SMA ...16 tahun yang lalu
-
Penalaran dalam Membuat Kesimpulan - PENALARAN DALAM MEMBUAT KESIMPULAN Proses berpikr manusia untuk menghubungkan hubungan data atau fakta yang ada sehingga sampai pada suatu kesimpulan diseb...16 tahun yang lalu
-
-
Internet And Business Online – The Act Of Interdependence - The best role of business online is that of interdependency. We’ve all heard the old saying, “No man is an island.” When it comes to online business this i...16 tahun yang lalu
-
DEBET KREDIT - Persamaan akuntansi terdiri dari sisi kiri dan sisi kanan yang dinamakan sisi kanan adalah DEBET dan sisi kiri adalah KREDIT .Setiap sisi Debet dan Kred...16 tahun yang lalu
-
Document Article
Network Hardware Connections
Ethernet uses star topology for the physical wiring layout. A diagram of a typical ethernet network layout is
shown below.
On a network, a hub is basically a repeater which is used to re-time and amplify the network signals. In this
diagram, please examine the hubs closely. On the left are 4 ports close to each other with an x above or below
them. This means that these ports are crossover ports. This crossover is similar to the arrangement that was used
for serial cables between two computers. Each serial port has a transmitter and receiver. Unless there was a null
modem connection between two serial ports, or the cable was wired to cross transmit to receive and vice versa,
the connection would not work. This is because the transmit port would be sending to the transmit port on the
other side.
Therefore note that you cannot connect two computers together with a straight network jumper cable between
their network cards. You must use a special crossover cable that you can buy at most computer stores and some
Network Hardware Connections
office supply stores for around 10 dollars. Otherwise, you must use a hub as shown here.
The hub on the upper left is full, but it has an uplink port on the right which lets it connect to another hub. The
uplink does not have a crossover connection and is designed to fit into a crossover connection on the next hub.
This way you can keep linking hubs to put computers on a network. Because each hub introduces some delay
onto the network signals, there is a limit to the number of hubs you can sequentially link. Also the computers that
are connected to the two hubs are on the same network and can talk to each other. All network traffic including all
broadcasts is passed through the hubs.
In the diagram, machine G has two network cards, eth0 and eth1. The cards eth1 and eth0 are on two different
networks or subnetworks. Unless machine G is programmed as a router or bridge, traffic will not pass between
the two networks. This means that machines X and Z cannot talk to machines A through F and vice versa.
Machine X can talk to Z and G, and machines A though F can talk to each other and they can talk to machine G.
All machines can talk to machine G. Therefore the machines are dependent on machine G to talk between the two
networks or subnets.
Each network card, called a network interface card (NIC) has a built in hardware address programmed by its
manufacturer. This is a 48 bit address and should be unique for each card. This address is called a media access
control (MAC) address. The media, in our specific case will be the ethernet. Therefore when you refer to
ethernet, you are referring to the type of network card, the cabling, the hubs, and the data packets being sent. You
are talking about the hardware that makes it work, along with the data that is physically sent on the wires.
There are three types of networks that are commonly heard about. They are ethernet, token-ring, and ARCnet.
Each one is described briefly here, although this document is mainly about ethernet.
Ethernet:
The network interface cards share a common cable. This cable structure does not need to form a structure, but
must be essentially common to all cards on the network. Before a card transmits, it listens for a break in traffic.
The cards have collision detection, and if the card detects a collision while trying to transmit, it will retry after
some random time interval.
Token Ring:
Token ring networks form a complete electrical loop, or ring. Around the ring are computers, called stations. The
cards, using their built in serial numbers, negotiate to determine what card will be the master interface card. This
card will create what is called a token, that will allow other cards to send data. Essentially, when a card with data
to send, receives a token, it sends its data to the next station up the ring to be relayed. The master interface will
then create a new token and the process begins again.
ARCnet:
ARCnet networks designate a master card. The master card keeps a table of active cards, polling each one
sequentially with transmit permission.
TCP/IP Ports and Addresses
TCP/IP Ports and Addresses
Each machine in the network shown below, has one or more network cards. The part of the network that does the job
of transporting and managing the data across the network is called TCP/IP which stands for Transmission Control
Protocol (TCP) and Internet Protocol (IP). There are other alternative mechanisms for managing network traffic, but
most, such as IPX/SPX for Netware, will not be described here in much detail. The IP layer requires a 4 (IPv4) or 6
(IPv6) byte address to be assigned to each network interface card on each computer. This can be done automatically
using network software such as dynamic host configuration protocol (DHCP) or by manually entering static addresses
into the computer.
Ports
The TCP layer requires what is called a port number to be assigned to each message. This way it can determine the
type of service being provided. Please be aware here, that when we are talking about "ports" we are not talking about
ports that are used for serial and parallel devices, or ports used for computer hardware control. These ports are merely
reference numbers used to define a service. For instance, port 23 is used for telnet services, and HTTP uses port 80 for
providing web browsing service. There is a group called the IANA (Internet Assigned Numbers Authority) that
controls the assigning of ports for specific services. There are some ports that are assigned, some reserved and many
unassigned which may be utilized by application programs. Port numbers are straight unsigned integer values which
range up to a value of 65535.
Addresses
Addresses are used to locate computers. It works almost like a house address. There is a numbering system to help the
mailman locate the proper house to deliver customer's mail to. Without an IP numbering system, it would not be
possible to determine where network data packets should go.
IPv4, which means internet protocol version 4, is described here. Each IP address is denoted by what is called dotted
decimal notation. This means there are four numbers, each separated by a dot. Each number represents a one byte
value with a possible mathematical range of 0-255. Briefly, the first one or two bytes, depending on the class of
network, generally will indicate the number of the network, the third byte indicates the number of the subnet, and the
fourth number indicates the host number. This numbering scheme will vary depending on the network and the
numbering method used such as Classless Inter-Domain Routing (CIDR) which is described later. The host number
cannot be 0 or 255. None of the numbers can be 255 and the first number cannot be 0. This is because broadcasting is
done with all bits set in some bytes. Broadcasting is a form of communication that all hosts on a network can read,
and is normally used for performing various network queries. An address of all 0's is not used, because when a
machine is booted that does not have a hardware address assigned, it provides 0.0.0.0 as its address until it receives its
assignment. This would occur for machines that are remote booted or those that boot using the dynamic host
configuration protocol (DHCP). The part of the IP address that defines the network is referred to as the network ID,
and the latter part of the IP address that defines the host address is referred to as the host ID.
IPv6 is an enhancement to the IPv4 standard due to the shortage of internet addresses. The dotted notation values are
increased to 12 bit values rather than byte (8 bit) values. This increases the effective range of each possible decimal
value to 4095. Of course the values of 0 and 4095 (all bits set) are generally reserved the same as with the IPv4
standard.
TCP/IP Ports and Addresses
An Example Network
In the diagram below, the earlier hardware wiring example is modified to show the network without the hubs. It also
shows IP addresses assigned to each interface card. As you can see there are two networks which are 192.168.1.x and
192.168.2.x. Machines A through F are on network 192.168.1.x. The machines X and Z are on network 192.168.2.x,
and machine G has access to both networks.
NIC A B C D E F G X Z
eth0 192.168.1.7 192.168.1.6 192.168.1.5 192.168.1.4 192.168.1.3 192.168.1.2 192.168.1.1 192.168.2.2 192.168.2.3
eth1 - - - - - - 192.168.2.1 - -
Using this port and addressing scheme, the networking system can pass data, addressing information, and type of
service information through the hardware, from one computer to another. The reason, there is an address for the
hardware card (ethernet address, also called MAC address), and another assigned address for that same card (IP
address), is to keep the parts of the network system that deal with the hardware and the software, independent of each
other. This is required in order to be able to configure the IP addressing dynamically. Otherwise, all computers would
have a static address and this would be very difficult to manage. Also, if a modification needs to be made to the
hardware addressing scheme for any reason, in ethernet, it will be transparent to the rest of the system. Conversely if a
TCP/IP Ports and Addresses
change is made to the software addressing scheme in the IP part of the system, the ethernet and TCP protocols will be
unaffected.
In the example above, machine F will send a telnet data packet to machine A. Roughly, the following steps occur.
1. The Telnet program in machine F prepares the data packet. This occurs in the application (Telnet),
presentation, and session layers of the OSI network model.
2. The TCP software adds a header with the port number, 23, to the packet. This occurs in the transport (TCP)
layer.
3. The IP software adds a header with the sender's and recipient's IP address, 192.168.1.2 to the packet. This
occurs in the network (IP) layer.
4. The ethernet header is added to the packet with the hardware address of the network card and the packet is
transmitted. This occurs in the link (Ethernet) layer.
5. Machine A's network card detects it's address in the packet, retrieves the data, and strips its header data and
sends it to the IP layer.
6. The IP layer looks at the IP header, and determines if the sender's IP address is acceptable to provide service to
(hosts.allow, hosts.deny, etc), and if so, strips the IP header and sends it to the TCP layer.
7. The TCP Layer reads the port number in it's header, determines if service is provided for that port, and what
application program is servicing that port. It strips the TCP header and passes the remainder of the data to the
telnet program on machine A.
Please note, that the network layers mentioned here are described in the next section. Also there are many types of
support at each of the four TCP/IP network system layers, but that issue is addressed in the next section.
0 komentar:
WEB LECTURE
WEB KAMPUS
Style Baju Muslim Murah
-
New September 2012 - [image: Rp150.000,00] DSC 1010 Rp145.000,00 [image: Rp145.000,00] DSC 1011 Rp145.000,00 DSC 1015 Rp150.000,00 DSC 1017 Rp150....13 tahun yang lalu
CV. LUANTJAR DJAJA

Luantjar Djaja
Perusahaan Luantjar Djaja didirikan pada tanggal…tahun 2004 sesuai akte pendirian no….Luantjar Dajaja berbentuk sebuah CV (perusahaan komanditer) yang bertempat di Delta sari indah no. 104 Waru-Sidoarjo. Pada tahap awal perusahaan ini masih digolongkan sebagai industri kecil menengah yang nantinya kami optimis akan menjadi sebuah perusahaan yang besar dan bersaing dengan perusahaan lainnya yang sejenis.
Kegiatan perusahaan kami bergerak di bidang jasa IT (Information Technology) baik sebagai konsultan maupun yang lainnya. Memang kami sadar bahwa perusahaan kami masih baru akan tetapi untuk kemampuan kami cukup bersaing.
Perusahaan kami cukup andal dalam hal tenaga kerja, ini dikarenakan semua tenaga kerja kami lulusan dari sebuah perguruan tinggi negeri yang berkompeten dalam IT.
Sehubungan dengan kebijakan pemerintah Indonesia menuju Indonesia Go Open Source (IGOS) dan penegakan UU HaKI (hak kekayaan intelektual) tentang pembajakan perangkat lunak yang masih merajalela di bumi Indonesia.
Linux Education Centre
Contac Person :
Adhytiya Handoko :
31-7885404,0856-3473261
Hormat kami
Directur Marketing Directur
Adhytia Handoko,A.Md M. & Syariefuddien Z, S.Pd.,M.T