Website YPPI - Education ICT in Surabaya
Download soft Jaringan
Download Buku LINUX
Download buku VIRUS
Donwload buku Programing
Download buku seputar jaringan
Download Ost Catatan Akhir Sekolah
Download Lagu Mandarin Full House
About Me

- information technology education
- I'm the man coming from the heroic city of surabaya and of full dedication to the world of education and information Technology in YPPI. I'm still willing to develop and empower my skill & knowedgle so as to step advanced for the nation's future
Blog Theacher SMA YPPI 1
-
ROBOT UNESA BERTANDING DI AMERIKA - Surabaya (beritajatim.com) - Satu lagi kebanggaan yang akan ditunjukan oleh putra-putri terbaik bangsa. Universitas Negeri Surabaya (Unesa) yang dikena...14 tahun yang lalu
-
Mengenali dan membasmi virus koplaz - Virus "K0pL4xZ" yang terdeteksi sebagai VBWorm.QTT mengincar pengguna komputer, khususnya yang memiliki banyak file Office, dengan cara mengganti icon dan ...15 tahun yang lalu
-
MATA PEMIMPIN - ada mata inderawi, ada mata budi, dan ada mata jiwa. Apakah persamaan yang dimiliki oleh tokoh-tokoh sekaliber Sir Winston Churchill, Soekarno, Mohammad Hat...14 tahun yang lalu
-
Resep Masakan Enak Sehari Hari - *Resep Masakan Enak Sehari Hari* http://digestivehealing.com/__media__/js/netsoltrademark.php?d=https://www.dapur-mbu.me/ http://educateboys.com/__media__...1 tahun yang lalu
-
-
gerak air laut - *Gerak Air Laut* Ada 3 gerakan air laut yang akan kita bahas yaitu: arus laut, gelombang laut, dan pasang surut air laut. 1. *Arus Laut* Arus laut (*se...15 tahun yang lalu
-
Saat Dimana Pendidikan Mulai Diputarbalikan Oleh Kepentingan Golongan - *Salam Pendidikan Indonesia.* Pendidikan adalah wadah dimana diciptakannya generasi-generasi bangsa yang kompeten dan berkarakter. Namun jaran...7 tahun yang lalu
-
Anda Dibentuk untuk Keluarga Allah - Persekutuan berarti terikat satu dng yg lain seperti kita terikat dengan Tuhan.Allah mengharapkan agar kita memberikan hidup kita satu kpd yg lain. Seperti...14 tahun yang lalu
-
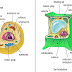
sel hewan dan tumbuhan - *A. Sel (Pendahuluan)* Gbr. Penampang Sel Hewan dan Sel Tumbuhan *Sahabat Amoeba ( Anak muda Biologi **) …,* tahukah kalian bahwa tubuh kita tersusun...14 tahun yang lalu
-
-
ABSTRAKSI PROPOSAL PTK 2007/2008 - PROPOSAL PROGRAM HIBAH PENINGKATAN MUTU PEMBELAJARAN UNIVERSITAS KATOLIK WIDYA MANDALA 2007/2008 PENGGUNAAN METODE PEMBELAJARAN KOOPERATIF MODEL STUDENT TE...15 tahun yang lalu
-
-
-
Mandikan aku Bunda.......... - Cerita ini sangat cocok sebagai bahan renungan bagi kita semua, terutama yang sehari-hari sangat disibukkan dengan aktivitas kerja dan profesi lainnya. Sem...14 tahun yang lalu
-
NARKOTIKA - Narkoba Dari Wikipedia bahasa Indonesia, ensiklopedia bebas Langsung ke: navigasi, cari Sebotol heroin yang merupakan salah satu narkoba yang paling dikena...8 tahun yang lalu
-
-
-
Honesty - Di jaman sekarang masih adakah orang jujur diketemukan?Mengapa begitu sulitnya menemukan orang jujur di muka bumi ini?Virus apakah yang telah menjangkiti a...14 tahun yang lalu
-
Tenzin Gyatso Zitate / 14TH DALAI LAMA tenzin gyatso INSPIRATIONAL QUOTE POSTER 24X36 kindness | eBay - Para las emociones destructivas, tenemos que ser conscientes de lo que da lugar a ellas y cuáles son los antídotos ~ tenzin gyatso, 14º dalai lama. Tenz...11 bulan yang lalu
-
-
8 kebohongan ibu yang positif - 8 KEBOHONGAN IBU Cerita bermula ketika aku masih kecil, aku terlahir sebagai seorang anak laki-laki di sebuah keluarga yang miskin. Bahkan untuk makan saja...14 tahun yang lalu
-
-
Ciri Orang Cerdas - Bagaimana menurut anda ciri – ciri orang Cerdas ? Apakah dia seorang dengan pendidikan Formal yang tinggi, ataukah Orang tersebut mempunyai pengalaman yang...15 tahun yang lalu
-
OPINI - MENCIPTAKAN SEKOLAH SEBAGAI ZONA NYAMAN BAGI SISWA Bagi siswa, suasana belajar di sekolah sangatlah tidak nyaman, beda dengan dunia luarnya yang dipenuhi d...14 tahun yang lalu
-
-
Pembelajaran Interaktif - *Pembelajaran Interaktif Merupakan Suatu Kebutuhan* *Theresia Henywati – Kepala SMA YPPI - I* Memasuki era global , pada tahun pelajaran 2008 / 2009 SMA ...15 tahun yang lalu
-
Penalaran dalam Membuat Kesimpulan - PENALARAN DALAM MEMBUAT KESIMPULAN Proses berpikr manusia untuk menghubungkan hubungan data atau fakta yang ada sehingga sampai pada suatu kesimpulan diseb...15 tahun yang lalu
-
-
Internet And Business Online – The Act Of Interdependence - The best role of business online is that of interdependency. We’ve all heard the old saying, “No man is an island.” When it comes to online business this i...14 tahun yang lalu
-
DEBET KREDIT - Persamaan akuntansi terdiri dari sisi kiri dan sisi kanan yang dinamakan sisi kanan adalah DEBET dan sisi kiri adalah KREDIT .Setiap sisi Debet dan Kred...14 tahun yang lalu
-
Surabaya (beritajatim.com) - Satu lagi kebanggaan yang akan ditunjukan oleh putra-putri terbaik bangsa. Universitas Negeri Surabaya (Unesa) yang dikenal "moncer" dalam mencetak Guru, kini juga mengirimkan mahasiswa berprestasinya mewakili Indonesia dalam perlombaan bergengsi di kancah internasional yaitu di Trinity College Hartford, Conecticut, Amerika.
Menurut salah satu anggota tim robot Dewo Unesa, Samsul Huda, tidak mudah bisa mewakili Indonesia di kancah internasional. Seperti diketahui robot Unesa yang diberi nama Dewo ini, sebelumnya telah berhasil memenangkan Kontes Robot Cerdas Indonesia (KRCI) di UGM pertengahan 2009 lalu.
"Karena memengkan kontes tingkat nasional inilah, kita akhirnya yang bisa mewakili Indonesia untuk bersaing di tingkat internasional", katanya.
Perlombaan robot tingkat internasional itu sendiri akan digelar pada 10-14 April. Tim robot dari Unesa akan berangkat pada tanggal 7 April 2010. Perlombaan ini hanya bisa diikuti oleh maksimal 2 tim dari satu negara.
Menurut pembina tim robot Dewo, Syarifudin Yuhri, total yang sudah mendaftar sampai saat ini adalah 172 tim. "Pendaftaran ini ditutup pada tanggal 1 April 2010," katanya.
Jumlah masiswa dalam tim robot Dewo adalah dua puluh, sedangkan nanti yang akan diberangkatkan ke Amerika hanya lima anggota, yaitu Samsul Huda, Apriliyano Suseno, M Kamim Munir, Mustika Dewi Prihastuti, dan Della Sagita. Mereka nanti akan ditemani para pembina yaitu dari dosen dan beberapa pejabat di lingkungan Unesa.
Menurut Samsul, karena lomba yang ada di Amerika ini berbeda dengan yang ada di UGM, yaitu KCRI maka, robot yang diberangkatkan nanti harus disesuaikan dengan kelas atau kriterianya. Robot Dewo adalah robot yang mempunyai tugas untuk menyelamatkan boneka dan meniup lilin, sedangkan di Amerika tugas dari robot adalah mencari lilin di ruang yang sudah ditentukan dan meniup lilin. "Jadi kita menyesuaikan dengan itu," kata Samsul.
Menurut pembina tim robot Dewo, Syarifudin Yuhri, perubahan yang terjadi tidak signifikan dan hanya menyesuaikan dengan yang diperlombakan. Tim robot unesa nanti akan membuat dua robot yang akan diperlombakan. Angaran yang diperlukan untuk membuat robot ini sekitar 284 juta.
Pihak kampus sendiri sudah mengelontarkan uang sebesar 300 juta untuk mendukung rencana membuat robot oleh mahasiswa Unesa ini. "Peluang kami 50:50 mas, tapi mudah-mudahan kita bisa jadi yang terbaik," sambungnya.
Ditemui beritajatim.com, Samsul menjelaskan, persiapan sampai detik ini sudah sekitar 75%. Yang masih menjadi PR berat hanya tentang Visa saja.
"Robot kami nanti juga namanya akan berganti, kalau dulu bernama Dewo sekarang bernama Barca dan Barca Kick. Kami mohon doannya agar kita bisa memberikan yang terbaik untuk Unesa dan Indonesia," tambahnya.(mif/eda)
Dikutip, dari berita jatim....
CCTV SEBAGAI SENSOR POSISI Untuk Dasar Implementasi Robot
0 komentar Ditulis oleh information technology education di 23.23Kamera CCTV adalah suatu kamera yang secara real time dapat diinputkan ke dalam computer.
Kamera CCTV sering diakai sebagai sarana untuk alat keamanan. Dalam penelitian ini kamera
CCTV difungsikan sebagai alat instrumentasi atau alat untuk menghitung jarak perpindahan suatu benda. Dengan mengubah citra ke dalam model threshold dan operasi template matching antara citra satu dengan citra duaakan menghsilkan citra yang menampilkan posisi benda awal dan posisi benda akhir. Kemudian diukur jarak piksel antara posisi benda awal dan posisi benda akhir.
Latar Belakang
Alat ukur atau alat instrumentasi banyak sekali dibutuhkan baik pada aplikasi industri
maupun rumah tangga. Hal ini seiring banyak sekali dipakainya aplikasi di bidang industi dan
rumah tangga yang memakai kendali umpan balik, atau dalam bahasa sehari-harinya adalah alat
otomatis. Pada salah satu teknik pengolahan citra memungkinkan citra digital hasil dari kamera
digital dapat difungsikan sebagai suatu alat ukur atau alat instrumentasi. Pengolahan citra tersebut adalah dengana mengubah citra digital kedalam model threshold sehingga didapat batasan pada citra tersebut. atau bisa juga memakai teknik deteksi tepi. Setelah mendapatkan batasan-batasan pada citra, kemudian dilakukan penentuan pedoman untuk instrumentasi. Sebagai contoh untuk mengukur perpindahan posisi suatu benda. Dilakukan dua buah citra digital, citra digital pertama adalah untuk penentuan jarak awal dan citra digital ke dua adalah untuk penentuan jarak akhir. Dengan mengubah citra ke dalam model threshold dan operasi template matching antara citra satu dan citra dua akan menghasilkan citra yang menampilkan posisi benda awal dan posisi benda akhir. Kemudian diukur jarak piksel antara posisi benda awal dan posisi benda akhir. Kamera CCTV adalah suatu kamera yang secara real time yang dapat diinputkan kedalam komputer. kamera CCTV sering dipakai sarana untuk alat keamanan. Dalam penelitian ini kamera CCTV difungsikan sebagai alat instrumentasi atau alat ukur, karena alat ini digunakan secara real time. Bagaimana kamera CCTV ini bisa difungsikan sebagai alat ukur atau alat instrumentasi mendorong peneliti melakukan analisa untuk memfungsikan kamera CCTV sebagai alat instrumentasi.
Kamera Sebagai Akusisi Citra
Dalam proses akusisi citra dikenal dengan trigger (picu), frame, log, start dan
stop. Start adalah mulai gambar atau kamera berjalan dalam display, untuk ini hanya
memerlukan monitor. Trigger adalah picu saat kapan frame mulai masuk kedalam
memori. Frame masuk ke dalam memori bisa disetting. Dalam hal ini
menunjukkan frame yang diakusisi adalah 3 frame tiap trigger. Trigger ini bisa diatur
pengulangan picu dalam video stream. Log adalah banyaknya frame yang masuk dalam
memori.
Kamera Sebagai Pengolahan gambar Morphologi
Morpologi adalah satu teknik pengolahan citra yang berdasakan pada bentuk obyek. Nilai dari
tiap piksel pada citra keluaran berasal dari operasi perbandingan suatu piksel dengan piksel-piksel disekitarnya (neighbors) pada citra masukan. Operasi perbandingan ini bergantung pada suatu struktur elemen. Struktur elemen adalah matrik yang digunakan untuk memberikan suatu tanda pada piksel-piksel di sekitar piksel asal (origin) dengan suatu bentuk dan ukuran tertentu. Matrik ini mempunyai bentuk dan ukuran yang bebas dan mempunyai nilai 1 dan 0. Operasi morphologi dapat dibagi menjadi dua operasi dasar, yaitu Erosi dan Dilasi.
Kamera Sebagai Dilasi
satu piksel disekeliling obyek tersebut. Proses ini menghasilkan area yang lebih besar dari obyek
tersebut.
Proses Dilasi dapat dinyatakan sebagai berikut :
E = B ⊕ S = {x,y|Sxy ∩ B ≠ Ø}
E adalah Citra Output. B adalah obyek dan S adalah Struktur elemen. Citra keluaran
didapat dari piksel asal / origin nilainya bertambah atau menjadi satu(jika nilainya satu
maka nilainya akan tetap satu) jika ada piksel tetangga (neighbors) sesuai dengan
struktur elemen.
Kamera sebagai Segmentasi
Segmentasi adalah suatu proses untuk memisahkan sejumlah objek dalam suatu citra dari latar
belakangnya. Proses segmentasi dapat dilakukan dengan menggunakan dua buah pendekatan
sebagai berikut :
• Metode berdasarkan tepi (edge–based)
Metode ini berbasiskan perbedaan atau perubahan mendadak nilai intensitas suatu piksel
terhadap piksel tetangganya.
• Metode berdasarkan daerah (region-based)
Metode ini berbasiskan kesamaan nilai suatu piksel terhadap piksel tetangganya.
akan pada citra biner.
Dapat kita Ketahui bersama
mengatur lagi repeat trigger.
vid,'FramesPerTrigger',1);
set(vid, 'TriggerRepeat',5);
Inisialisasi repeattrigger memakai 5 frame, hal ini disesuaikan dengan frame rate hardwarenya. Atau dengan kata lain dalam 1 detik alat ini mampu mengakusisi gambar sebanyak 5 frame. Data yang diakusisi ke memori adalah 1 frame. Input gambar yang diambil disamakan dengan inisialisasi repeat trigger.
data = getdata(vid,1);
Gambar pertama adalah untuk gambar pada posisi benda saat pertama kali diambil atau diambil
gambarnya. Gambar atau frame pertama ini yang kemudian menjadi gambar yang diinputkan ke memori. Sebelum diinputkan ke memori dilakukan operasi biner yaitu membuat gambar menjadi bernilai 0 dan 1.
I = rgb2gray(data);
threshold = graythresh(I);
master = im2bw(I,threshold);
Cara mengetahui adanya pergerakan adalah sebagai berikut :
for i= 1 : 320
for j = 1 : 240
L(i,j) = data2(i,j) - master(i,j);
if L(i,j) == 1;
master2 = L;
else
flushdata(vid);
end
L adalah gambar yang diinputkan untuk dilakukan pengujian. Ukuran gambar yang dipakai
adalah 320x240. flushdata bertujuan untuk menghapus semua gambar di memori.
Sumber .
Seminar Nasional Teknologi 2007 (SNT 2007)
Erdhi Widyarto Nugroho
SEMINAR ROBOT DI FAKULTAS FT UNESA PENUH PEMINAT....
0 komentar Ditulis oleh information technology education di 22.12Ass Wr..Wb serta salam Sejahtera.... amien.
Seminar dengan pembicara Pakar robot Nasional sekaligus Juri Kontes Robot Di Indonesia Dr.,Ir. Endra Pitowarno, M.Eng di gedung A1 lantai2 dimulai jam 05.00 ruang seminar Fakultas Teknik Universitas negeri Surabaya, yang digelar team robot unesa yang dipromotori team DEWO Fakultas teknik dalam rangka persiapan team robot dewo untuk berlomba di Kontes Robot dunia tahun 20010 di Trinity College University Amerika Serikat Trinity College Fire-Fighting Robot Contest Hartford, Connecticut, Amerika Serikat , serta sosialisasi robot di lingkungan kampus serta recrutmen team robot untuk mengikuti lomba robot nasional KRCI dan KRSI 2010 , yang mendapatkan dukungan penuh oleh universitas. Memberikan hasil maksimal karena banyak mahasiswa yang memberikan respon yang antusias, sehingga ruang seminar dipenuhi undangan maupun peserta.
Dalam hal ini pembicara memberikan gambaran secara luas mengenai robot serta sejarah tentang robot itu sendiri, dengan demikian akan dapat memberikan gambaran yang sangat berarti untuk mahasiswa fakultas teknik. Kami yakin temen- temen mahasiswa masih ingin membantu meneruskan perjuangan kami di tahun 2010 nantinya.
Dan untuk temen temen mahasiswa yang ingin meneruskan perjuangan kami dan ingin menjadi bagian team robot fakultas teknik unesa. Kami juga mengadakan recrutmen dengan mengisi form pendaftaran dan materi kuisioner bakat dan minat untuk tahap seleksi.
Untuk Informasi Silahkan ke sekertariatan robot DEWO Fakultas Teknik di Lap MECHATRONIKA Fak Teknik Mesin Gedung A6 lantai 1 belakang BEM Mesin.
Untuk Menjadi Team Robot Seleksi akan dilakukan Beberapa Tahap :
1. Mengisi Kuisioner bakat dan minat tanggal 21-22 oktober 2009 s/d jam 12 siang.
2. Tes Wawancara dengan Dosen terpilih, dan Pembina Robot.
3. Tes Phisikology.
4. Tes lain yang akan ditentukan panitia Recrutment.
Setelah lolos Tes tersebut maka, peserta bisa mejanutkan tes berikutnya sesuai ketentuan dalam Team robot, yang akan di informasikan selanjutnya.
Terimakasih yang sangat dalam untuk Dr.,Ir. Endra Pitowarno, M.Eng, manager team selaku Ketua Jurusan Teknik Elektro Drs. Edy Sulistyo, M.Pd, Pembina Robot M. Syariefuddien Z, S.Pd., MT. dan Mr Agung Priyo Budiono Dari Mechatronika Fak Teknik Mesin, Serta Semua Dosen dan Temen - temen Team Dewo Robot, Dan Temen Mahasiswa yang saya hormati.
Semoga dunia robotika di Universitas Negeri Surabaya tetap jaya, Amien.
Salam dari penulis.
Dewo team, ADI WINARNO, A.Md
Jatim Borong Juara Kontes Robot Tingkat Nasional
0 komentar Ditulis oleh information technology education di 08.00SURABAYA - Tim robot dari perguruan tinggi di Jawa Timur kembali menorehkan prestasi nasional dalam Kontes Robot Indonesia (KRI), Kontes Robot Cerdas Indonesia (KRCI), dan Kontes Robot Seni Indonesia (KRSI) 2009 di Graha Sabha Pramana Universitas Gadjah Mada (UGM) Yogyakarta yang berakhir kemarin (14/6). Dalam kontes robot bergengsi antarkampus yang diselenggarakan Dikti Depdiknas yang diikuti 24 tim itu, tim PENS-ITS Surabaya kembali menjadi juara dan berhak mewakili Indonesia dalam di ABU ROBOCON 2009 Tokyo, Jepang, Agustus nanti.
Tim robot PENS-ITS yang menjadi juara KRI itu adalah robot D4=S1. Sebelumnya, robot itu merupakan pemenang pertama saat seleksi wilayah regional IV (Jatim dan Indonesia Timur) di kampus ITS pada Mei 2009 lalu.
Tidak hanya di KRI yang juara pertamanya direbut kampus Jatim. Juara KRCI dan KRSI juga disapu bersih tim asal Jatim. Untuk KRCI, robot Dewo dari Universitas Negeri Surabaya (Unesa) menjadi juara 1. Sedangkan KRSI, diraih oleh tim robot Elit dari Institut Teknologi Nasional (ITN) Malang.
Joko Suwito, pendamping tim robot Unesa, kemarin menceritakan, dalam pertandingan final KRI, tim D4=S1 bertemu dengan robot Patriot dari UGM. Dalam final itu, tim D4=S1 sempat mengalami error pada robot traveler ketika akan memukul bedug.
Sedang tim Patriot sudah makin mendekati di belakangnya. Beruntung, tim D4=S1 sigap melakukan retry. Robot karya mahasiswa ITS itu pun berhasil mencapai goal dengan memukul ketiga bedug secara sempurna.
Dengan keberhasilan mencapai goal lebih dulu, tepatnya di detik ke-52, tim D4=S1 dari PENS-ITS akhirnya dinyatakan sebagai juara pertama. "Tepuk tangan pun bergemuruh di ruang pertandingan. Tim-tim kampus dari Jatim juga ikut bangga atas keberhasilan itu," ujar Joko dihubungi Jawa PosJambi Independent) melalui ponselnya kemarin. (induk
Bayu Prasetyo, ketua tim D4=S1, mengatakan bahwa pihaknya bersyukur bisa menjuarai KRI itu. "Yang jelas, kami sangat bersyukur bisa menang. Semua musuh kami berat-berat. Kami sempat khawatir tidak akan menang," katanya. Meski begitu, pihaknya mengaku belum puas dengan catatan waktu yang diraih. "Catatan waktu kami 52 detik," ujarnya.
Tim robot Dewo Unesa sukses menjuarai KRCI setelah pada babak semifinal berhadapan dengan tim-tim robot yang termasuk unggulan, di antaranya robot Ghen JR (PENS ITS), Djodja X01 (UGM), dan A BENK (Politeknik Bengkalis Riau).
Joko mengatakan, timnya layak menang karena sudah disiapkan secara matang. Butuh waktu cukup lama untuk mempersiapkan lomba tersebut. Untuk mengikuti lomba itu, robot Dewo pun harus diganti total, mulai dari sensor, serfomotor, hingga baterai. "Hampir semua kita ganti,” jelas pembantu dekan III Fakultas Teknik Unesa itu.
Jawapost - 15 juni 2009
Menurut Joko, yang paling dipersiapkan matang adalah baterai, sebab kekalahan tim robot tersebut saat bertanding pada perlombaan lalu berada pada baterai, sehingga pihaknya harus mempersiapkan bateri secara matang. “Kita sudah antisipasi baterai, jangan sampai mogok karena kehabisan baterai,” ujarnya.
Selain itu, pihaknya juga menggunakan berbagai strategi untuk memenangkan perlombaan tersebut. Dalam lomba itu, robot tidak cukup hanya bisa berjalan cepat. Robot juga harus bisa mengambil boneka yang sudah dipasang di tempat yang sudah ditentukan. Namun sebelum bisa mengambil boneka, robot tersebut harus terlebih dulu memadamkan lilin yang ada.
Joko berharap kemenangan tersebut bisa terus dipertahankan, dengan terus mengembangkan teknologi robot dan terus berlatih untuk mengembangkan robot. "Mempertahankan itu lebih susah daripada mendapatkan,” jelas Joko.(jpnn)
ARCnet Network ARCnet (Attached Resource Computer Network) (CR)
0 komentar Ditulis oleh information technology education di 12.21ARCnet Network
ARCnet (Attached Resource Computer Network)
(CR)
Topology is star and bus or a mixture. Cable type is RG-62 A/U coaxial (93 ohm), UTP or fiber-optic. A
network can use any combination of this media. Connectors used include BNC, RJ-45, and others. It
passes tokens passing for media access. Maximum segment length is 600 meters with RG-62 A/U, 121
meters with UTP, 3485 meters with fiber-optic, and 30 meters from a passive hub. The specification is
ANSI 878.1. It can have up to 255 nodes per network. The speed is 2.5 Mbps. ARCnet Plus has operating
speeds approaching 20Mbps.
Signals are broadcast across the entire network with computers processing only signals addressed to
them. ARCnet tokens travel based on a station identifier (SID) which each computer has. Each network
card has a DIP switch used to set the SID with an address between 1 and 255. Signals are generally sent
from the lowest numbered station to the next until they wrap around back to SID of 1. To determine nonexistent
stations, the station with the lowest ID indicates it has the token and begins querying IDs of
higher value until it gets a response. Then the next computer does the same until the original station is
queried. This procedure is done when a station is added or removed from the network or when the
network is originally started. How does the network know when a station has been added or removed?
How is the lowest numbered SID identified? Addresses assignment is based on proximity, which helps
the network operate more efficiently.
The acronym SID is used for a station identifier with regard to ARCnet, but as used in the Windows NT
and Windows 95 operating systems, it refers to the security identification number of a user or group.
AppleTalk Network
AppleTalk Network
Topology is bus. Cable type is STP. The connectors are specialized. The media access method is
CSMA/CA . Maximum segment and network length is 300 meters. The maximum number of connected
segments is 8. There are 32 maximum nodes per segment with 254 maximum number of nodes per
network. Speed is 230.4Kbps. The cabling system used with AppleTalk is called LocalTalk.
Addressing
Addressing is dynamic with each computer, when powered on, choosing its last used address or a random
address. The computer broadcasts that address to determine if the address is used. If it is used, it will
broadcast another random address until it finds an unused address.
EtherTalk and TokenTalk provide for use of AppleTalk network protocols on top of ethernet and token
ring architectures respectively.
LocalTalk
LocalTalk uses STP cable and bus topology. Using CSMA/CA for media access, computers will first
determine if any other computers are transmitting, before they transmit. A packet is transmitted prior to
transmitting that alerts other computers that a transmission will be sent. Usually LocalTalk is only used
in small environments.
FDDI
FDDI
Fiber Distributed Data Interface (FDDI)
Standard is ANSI X3T9.5 . Topology is ring with two counter rotating rings for reliability with no
hubs. Cable type is fiber-optic. Connectors are specialized. The media access method is token passing.
The maximum length is 100 kilometers. The maximum number of nodes on the network is 500. Speed is
100 Mbps. FDDI is normally used as a backbone to link other networks. A typical FDDI network can
include servers, concentrators, and links to other networks.
Devices called concentrators provide functions similar to hubs. Most concentrators use dual attachment
station network cards but single attachment concentrators may be used to attach more workstations to the
network.
FDDI token passing allows multiple frames to circulate around the ring at the same time. Priority levels
of a data frame and token can be set to allow servers to send more data frames. Time sensitive data may
also be given higher priority. The second ring in a FDDI network is a method of adjusting when there are
breaks in the cable. The primary ring is normally used, but if the nearest downstream neighbor stops
responding the data is sent on the secondary ring in attempt to reach the computer. Therefore a break in
the cable will result in the secondary ring being used. There are two network cards which are:
1. Dual attachment stations (DAS) used for servers and concentrators are attached to both rings.
2. Single Attachment stations (SAS) attached to one ring and used to attach workstations to
concentrators.
A router or switch can link an FDDI network to a local area network (LAN). Normally FDDI is used to
link LANs together since it covers long distances.
IPX/SPX
IPX/SPX
IPX/SPX is a routable protocol and can be used for small and large networks. The following protocols
are part of the IPX/SPX suite:
l SAP - Service Advertising Protocol packets are used by file and print servers to periodically
advertise the address of the server and the services available. It works at the application,
presentation, and session levels.
l NCP - NetWare Core Protocol provides for client/server interactions such as file and print
sharing. It works at the application, presentation, and session levels.
l SPX - Sequenced Packet Exchange operates at the transport layer providing connection oriented
communication on top of IPX.
l IPX - Internetwork Packet Exchange supports the transport and network layers of the OSI
network model. Provides for network addressing and routing. It provides fast, unreliable,
communication with network nodes using a connection less datagram service.
l RIP - Routing Information Protocol is the default routing protocol for IPX/SPX networks which
operates at the network layer. A distance-vector algorithm is used to calculate the best route for a
packet.
l ODI - Open Data-link Interface operates at the data link layer allowing IPX to work with any
network interface card.
NetWare frame types
Novell NetWare 2.x and 3.x use Ethernet 802.3 as their default frame type. Novell NetWare 4.x networks
use Ethernet 802.2 as their default frame type. If communication does not occur between two NetWare
computers it is a good idea to check the netware versions of the two computers to be sure their frame
types match. If the frame types do not match on an ethernet network, the computers cannot communicate.
NetBEUI
NetBEUI
In order to properly describe NetBEUI, the transport protocol sometimes used for Microsoft networking,
it is necessary to describe Microsoft networking in some detail and the various protocols used and what
network layers they support.
NetBIOS, NetBEUI, and SMB are Microsoft Protocols used to support Microsoft Networking. The
NetBIOS stack includes SMB, NetBIOS, and NetBEUI which are described in the table below. The
following are parts of the Microsoft networking stack:
Name Network Layer Description
Redirector Application
Directs requests for network resources to the appropriate
server and makes network resources seem to be local
resources.
SMB Presentation
Server Message Block provides redirector client to server
communication
NetBIOS Session
Controls the sessions between computers and maintains
connections.
NetBEUI Transport, Network
Provides data transportation. It is not a routable transport
protocol which is why NBT exists on large networks to use
routable TCP protocol on large networks. This protocol may
sometimes be called the NetBIOS frame (NBF) protocol.
NDIS and NIC driver Data Link
NDIS allows several adapter drivers to use any number of
transport protocols. The NIC driver is the driver software for
the network card.
NetBIOS Extended User Interface (NetBEUI)
This is a separate protocol from NetBIOS. It supports small to medium networks providing transport and
network layer support. It is fast and small and works well for the DOS operating system but NetBEUI is
not a routable protocol.
Name Resolution
There are three methods of mapping NetBIOS names to IP addresses on small networks that don't
perform routing:
1. IP broadcasting - A data packet with the NetBIOS computer name is broadcast when an
associated address is not in the local cache. The host who has that name returns its address.
NetBEUI
2. The lmhosts file - This is a file that maps IP addresses and NetBIOS computer names.
3. NBNS - NetBIOS Name Server. A server that maps NetBIOS names to IP addresses. This service
is provided by the nmbd daemon on Linux.
System wide methods of resolving NetBIOS names to IP addresses are:
1. b-node - Broadcast node
2. p-node - Point-to-point node queries an NBNS name server to resolve addresses.
3. m-node - First uses broadcasts, then falls back to querying an NBNS name server.
4. h-node - The system first attempts to query an NBNS name server, then falls back to broadcasts if
the nameserver fails. As a last resort, it will look for the lmhosts file locally.
NetBIOS name services use port 137 and NetBIOS session services use port 139. NetBIOS datagram
service uses port 138.
To resolve addresses from names, a computer on a Microsoft network will check its cache to see if the
address of the computer it wants to connect to is listed there. If not it sends a NetBIOS broadcast
requesting the computer with the name to respond with its hardware address. When the address is
received, NetBIOS will start a session between the computers. On larger networks that use routers, this is
a problem since routers do not forward broadcasts, nor is NetBEUI a routable protocol. Therefore
Microsoft implemented another method of resolving names with the Windows Internet Name Service
(WINS). The following steps are taken to resolve NetBIOS names to IP addresses for H-node resolution
on larger networks using TCP/IP (NBT):
1. NetBIOS name cache
2. WINS Server
3. NetBIOS broadcast
4. lmhosts file
5. hosts file
6. DNS server
For a more complete explanation of NetBIOS name resolution, WINS, and Windows networking in
general, see the manuals in the Windows operating system section such as the "Windows TCP/IP
Reference." Also a Windows Networking manual will be written for this section.
NetBIOS over TCP/IP (NBT)
Since NetBEUI is not a routable protocol, Microsoft implemented NBT for larger networks. NetBIOS
messages are normally encapsulated in NetBEUI datagrams, but when using NBT, they are encapsulated
in TCP/IP datagrams. The NBT protocol is defined by RFC 1001 and RFC 1002.
NetBEUI
NWLink
NWLink is Microsoft's implementation of IPX/SPX. NWLink will act as a transport mechanism for
NetBIOS similar to the use of TCP/IP described in the NBT section above. NWLink is normally used to
support medium networks and may be used where NetWare servers are present.
Windows Internet Name Service (WINS)
WINS is the Microsoft implementation of NetBIOS name service. Samba on Linux can be used as a
WINS server.
Computers configured to use WINS, when booted, contact the WINS name server and give the server
their NetBIOS name and IP address. The WINS server adds the information to its database and it may
send the information to other WINS servers on your network. When a computer that is configured to use
WINS needs to get an address of another computer, it will contact the WINS server for the information.
Without the use of a WINS server, NetBIOS will only be able to see computers on the unrouted sections
of the local network. Does this mean a WINS server must exist in each routed section of the network?
The answer is no. This is because WINS uses TCP/IP which is routable. Only one WINS server needs to
exist on the network.
The Windows Networking Environment
A domain in a Microsoft networking environment refers to a collection of computers using user level
security. It is not the same as the term domain used with regard to the domain name system (DNS).
Domain related terms are:
l BDC - Backup Domain Controller is a backup for a PDC
l TLD - Top Level domain
l PDC - Primary Domain Controller is an NT server providing central control of user access
permissions and accounts on a network.
AppleTalk Protocols
AppleTalk Protocols
AppleTalk is the architecture used on with Apple brand computers and is a suite of protocols for
networking Apple computers. Some of the protocols are:
l AppleShare - Works at the application layer to provide services.
l AFP - AppleTalk Filing protocol - Makes network files appear local by managing file sharing at
the presentation layer.
l ATP - AppleTalk Transaction Protocol provides a Transport Layer connection between
computers. Three transaction layers:
m transaction requires (TREQ)
m transaction response (TRESP)
m transaction release (TREL)
l DDP - Datagram Delivery Protocol is a routable protocol that provides for data packet
transportation. It operates at the network layer at the same level of the IP protocol.
The AppleTalk networking scheme puts computers into groups called zones. This is similar to
workgroups on a Windows network.
Four Session layer protocols
l ASP - AppleTalk session protocol controls the starting and ending of sessions between computers
called nodes. It works at the session level. The NBP, described below is used to get addresses
from computer names. ATP is used at the transport level.
l ADSP - AppleTalk data stream protocol manages the flow of data between two established socket
connections.
l ZIP - Zone information protocol used with RTMP to map zones. Routers use zone information
tables (ZITs) to define network addresses and zone names.
l PAP - Printer access protocol manages information between workstations and printers.
Other Protocols
l NBP - Name-binding protocol translates addresses into names.
l AEP - AppleTalk echo protocol uses echoes to tell if a computer, or node, is available.
l RTMP - Routing table maintenance protocol is used to update routers with information about
network status and address tables. The whole address table is sent across the network.
l ARUP - AppleTalk update routing is a newer version of RTMP.
System Network Architecture
System Network Architecture
System Network Architecture (SNA) by IBM is a suite of protocols mainly used with IBM mainframe
and AS/400 computers. Two SNA protocols are:
l APPC - Advanced Peer-to-Peer Communications provides peer to peer services at the transport
and session layer.
l APPN - Advanced Peer-to-Peer Networking supports the computer connections at the network
and transport layers.
Microsoft produced the SNA Server so PC networks could connect with SNA networks.
SNA Layers
SNA has its own network model which is:
l Physical
l Data link - Uses protocols such as token-ring or Synchronous Data Link Control (SDLC).
l Path Control - Performs routing, division, and re-assembly of data packets.
l Transmission - Connection software
l Data flow - Prevents data overflows by monitoring and handling traffic
l Presentation - Handles interfaces to applications
l Transaction - Provides an interface for applications to use network services
SNA Network Devices
l host systems
l terminals
l Output devices
l Communications controllers
l Cluster controllers - Allow many devices to connect through them. They connect ot a host or
communications controller.
SNA Network Categories
l Nodes
m Type 2 - PCs, terminals and printers
m Type 4 - Communications controllers
m type 5 - Host computers used to manage the network
l Data links - Connection between combinations of hosts, cluster controllers, or nodes.
System Network Architecture
Possible SNA communications architectures
l SDLS - Synchronous Data Link Control
l BSC - Binary Synchronous Communication sends bits in frames which are timed sequences of
data.
l Token-ring
l X.25
l Ethernet
l FDDI
SNA units
NAU - Network Addressable Units
l LU - Logical Units are ports that users use to access network resources
m Type 1 - An interactive batch session
m Type 2 - An IBM 3270 terminal
m Type 3 - An IBM 3270 printer
m Type 6.2 - A program to program session
m Type 7 - An IBM 5250 family session
l PU - Physical Units are a network device used to communicate with hosts.
m Type 2 - Cluster controllers
m Type 3 - Front end process
m Type 5 - Host communications software
SNA software components
l SSCP - Systems Services Control Point manages all resources in the host's domain.
l NCP - Network Control Program performs routing, session management tasks. It runs in the
communications controller.
Other Transport Protocols
Other Transport Protocols
DECnet
DECnet from Digital Equipment Corporation is a suite of protocols which may be used on large
networks that integrate mainframe and minicomputer systems. It is a routable protocol. DNA - Digital
Network Architecture.
Data Link Control (DLC)
This protocol operates at the data link layer and is designed for communications between Hewlett-
Packard network printers and IBM mainframe computers. This protocol is not routable.
Open Systems Interconnect (OSI)
A suite of protocols developed by the International Standards Organization (ISO) which corresponds
with the layers of the OSI model. These protocols provide a number of application protocols for various
functions. The OSI protocol stack may be used to connect large systems. OSI is a routable transport
protocol.
Network Routing
Network Routing
Simple Networking Routing and Routers
This section will explain routing in simple terms with some simple standard rules. There may be exceptions to
these rules, but for introductory purposes we will keep the first example simple. Please be aware, that the
examples in this section are working examples, but more complexity may be added when a larger network is
considered, and multiple data routes become available.
Each network interface card (NIC) has a specific address which is an IP address or number. When data is sent
between two computers, the data must be sent in a package that has the address of the intended receiver (IP) on it.
It is like an envelope (ethernet) with the sender's and recipient's address on it. There is somewhat of a difference,
however. When the computer intends to send a packet, it first checks its routing table to see if the intended data
must be sent through a gateway. Many computers only have a simple routing table, which is built from the
network mask and the gateway information entered, when you set your computer up to do networking. The
computer, when set up for networking, must be assigned an IP address, netmask, and default gateway. This may
be done manually or done automatically using Dynamic Host Configuration Protocol (DHCP) to assign this
information to the computer when it boots. DCHP is described in another section. If the computer determines that
the packet must be sent to a gateway, it puts it in a special packet (ethernet) for that gateway, with the actual
recipient's address wrapped inside.
In the above paragraph, data packets are equated to a letter with an envelope. For this type of thinking, the
envelope would be similar to the ethernet, SLIP, or PPP packet which encapsulates the IP packet. The IP packet
and its encapsulated data would similar to a letter. Here's generally what happens when a package is sent:
The sending computer checks the IP part of the package to see the sender's IP address, and based on
the address and instructions in its routing table will do one of the following:
1. Send the packet to the ethernet address of the intended recipient. The following will happen:
1. The ethernet card on the receiving computer will accept the packet.
2. The other network levels (IP, TCP) will open the packet and use it according to filtering and other
programming instructions.
2. Send the packet to the ethernet address of a router, depending on the instructions in the routing table.
1. The ethernet card on the router will accept the packet.
2. The IP level of the router will look at the packet's IP address and determine according to its routing
table where to send the packet next. It should send it to another router or to the actual recipient.
3. The router will encapsulate the IP packet in another ethernet packet with the ethernet address of the
next router or the intended recipient.
4. Router hops will continue until the packet is sent on a network where the intended recipient is
physically located unless the packet expires.
5. The ethernet card on the receiving computer will accept the packet.
6. The other network levels (IP, TCP) will open the packet and use it according to filtering and other
programming instructions.
Network Routing
Lets say you enter an IP address of 10.1.20.45 and a netmask of 255.255.0.0. This means you are on the network
10.1.0.0 (I show it as 10.1.x.x, the X's mean don't care conditions). The machine's IP address and netmask,
together define the network, that it's NIC is on. Therefore any machine that fits in the address range provided
under 10.1.x.x can be accessed directly from your NIC, and any that are not in this number range, such as
10.3.34.67 cannot be accessed directly and must be sent to a gateway machine since it is on another network.
Typically most machines will use their netmask to make this determination which means if the address does not
match their known network, the package will be sent to that machine's default gateway in a special package meant
for a router. It works similar to a post office. When you send a letter in your town, you put it in the local slot. It
can be delivered to someone else in your town (network), but if you are sending to another town (network), you
put the letter in the out of town slot (default gateway), then the mail personnel put it in a special container or box
and send it to a main town (gateway), which then decides where to send it based on its address. Although this
simple network and default gateway may be common, specific computers or gateways can have much more
complex rules for routing that allow exceptions to this example.
Please be aware that in order to be forwarded, data packets must be addressed to a router. They cannot just be sent
to the recipient's address out to a network. The router does not pick packets off the network and forward them. If
a packet is sent on a network and a valid recipient is not on that network, there will be no response. This will be
demonstrated in the next section where a subnetwork will be described.
To keep routing simple, most networks are structured as shown below. Generally, the higher networks are
10.x.x.x, then the next are 10.0-254.x.x, then 10.0-254.0-254.x. The number 10 is used as an example Class A
network. This numbering scheme keeps routing simple and is the least confusing but networks can be set up in
other ways. In the diagram below, only gateways and their networks are shown.
Network Hardware Connections
Ethernet uses star topology for the physical wiring layout. A diagram of a typical ethernet network layout is
shown below.
On a network, a hub is basically a repeater which is used to re-time and amplify the network signals. In this
diagram, please examine the hubs closely. On the left are 4 ports close to each other with an x above or below
them. This means that these ports are crossover ports. This crossover is similar to the arrangement that was used
for serial cables between two computers. Each serial port has a transmitter and receiver. Unless there was a null
modem connection between two serial ports, or the cable was wired to cross transmit to receive and vice versa,
the connection would not work. This is because the transmit port would be sending to the transmit port on the
other side.
Therefore note that you cannot connect two computers together with a straight network jumper cable between
their network cards. You must use a special crossover cable that you can buy at most computer stores and some
Network Hardware Connections
office supply stores for around 10 dollars. Otherwise, you must use a hub as shown here.
The hub on the upper left is full, but it has an uplink port on the right which lets it connect to another hub. The
uplink does not have a crossover connection and is designed to fit into a crossover connection on the next hub.
This way you can keep linking hubs to put computers on a network. Because each hub introduces some delay
onto the network signals, there is a limit to the number of hubs you can sequentially link. Also the computers that
are connected to the two hubs are on the same network and can talk to each other. All network traffic including all
broadcasts is passed through the hubs.
In the diagram, machine G has two network cards, eth0 and eth1. The cards eth1 and eth0 are on two different
networks or subnetworks. Unless machine G is programmed as a router or bridge, traffic will not pass between
the two networks. This means that machines X and Z cannot talk to machines A through F and vice versa.
Machine X can talk to Z and G, and machines A though F can talk to each other and they can talk to machine G.
All machines can talk to machine G. Therefore the machines are dependent on machine G to talk between the two
networks or subnets.
Each network card, called a network interface card (NIC) has a built in hardware address programmed by its
manufacturer. This is a 48 bit address and should be unique for each card. This address is called a media access
control (MAC) address. The media, in our specific case will be the ethernet. Therefore when you refer to
ethernet, you are referring to the type of network card, the cabling, the hubs, and the data packets being sent. You
are talking about the hardware that makes it work, along with the data that is physically sent on the wires.
There are three types of networks that are commonly heard about. They are ethernet, token-ring, and ARCnet.
Each one is described briefly here, although this document is mainly about ethernet.
Ethernet:
The network interface cards share a common cable. This cable structure does not need to form a structure, but
must be essentially common to all cards on the network. Before a card transmits, it listens for a break in traffic.
The cards have collision detection, and if the card detects a collision while trying to transmit, it will retry after
some random time interval.
Token Ring:
Token ring networks form a complete electrical loop, or ring. Around the ring are computers, called stations. The
cards, using their built in serial numbers, negotiate to determine what card will be the master interface card. This
card will create what is called a token, that will allow other cards to send data. Essentially, when a card with data
to send, receives a token, it sends its data to the next station up the ring to be relayed. The master interface will
then create a new token and the process begins again.
ARCnet:
ARCnet networks designate a master card. The master card keeps a table of active cards, polling each one
sequentially with transmit permission.
TCP/IP Ports and Addresses
TCP/IP Ports and Addresses
Each machine in the network shown below, has one or more network cards. The part of the network that does the job
of transporting and managing the data across the network is called TCP/IP which stands for Transmission Control
Protocol (TCP) and Internet Protocol (IP). There are other alternative mechanisms for managing network traffic, but
most, such as IPX/SPX for Netware, will not be described here in much detail. The IP layer requires a 4 (IPv4) or 6
(IPv6) byte address to be assigned to each network interface card on each computer. This can be done automatically
using network software such as dynamic host configuration protocol (DHCP) or by manually entering static addresses
into the computer.
Ports
The TCP layer requires what is called a port number to be assigned to each message. This way it can determine the
type of service being provided. Please be aware here, that when we are talking about "ports" we are not talking about
ports that are used for serial and parallel devices, or ports used for computer hardware control. These ports are merely
reference numbers used to define a service. For instance, port 23 is used for telnet services, and HTTP uses port 80 for
providing web browsing service. There is a group called the IANA (Internet Assigned Numbers Authority) that
controls the assigning of ports for specific services. There are some ports that are assigned, some reserved and many
unassigned which may be utilized by application programs. Port numbers are straight unsigned integer values which
range up to a value of 65535.
Addresses
Addresses are used to locate computers. It works almost like a house address. There is a numbering system to help the
mailman locate the proper house to deliver customer's mail to. Without an IP numbering system, it would not be
possible to determine where network data packets should go.
IPv4, which means internet protocol version 4, is described here. Each IP address is denoted by what is called dotted
decimal notation. This means there are four numbers, each separated by a dot. Each number represents a one byte
value with a possible mathematical range of 0-255. Briefly, the first one or two bytes, depending on the class of
network, generally will indicate the number of the network, the third byte indicates the number of the subnet, and the
fourth number indicates the host number. This numbering scheme will vary depending on the network and the
numbering method used such as Classless Inter-Domain Routing (CIDR) which is described later. The host number
cannot be 0 or 255. None of the numbers can be 255 and the first number cannot be 0. This is because broadcasting is
done with all bits set in some bytes. Broadcasting is a form of communication that all hosts on a network can read,
and is normally used for performing various network queries. An address of all 0's is not used, because when a
machine is booted that does not have a hardware address assigned, it provides 0.0.0.0 as its address until it receives its
assignment. This would occur for machines that are remote booted or those that boot using the dynamic host
configuration protocol (DHCP). The part of the IP address that defines the network is referred to as the network ID,
and the latter part of the IP address that defines the host address is referred to as the host ID.
IPv6 is an enhancement to the IPv4 standard due to the shortage of internet addresses. The dotted notation values are
increased to 12 bit values rather than byte (8 bit) values. This increases the effective range of each possible decimal
value to 4095. Of course the values of 0 and 4095 (all bits set) are generally reserved the same as with the IPv4
standard.
TCP/IP Ports and Addresses
An Example Network
In the diagram below, the earlier hardware wiring example is modified to show the network without the hubs. It also
shows IP addresses assigned to each interface card. As you can see there are two networks which are 192.168.1.x and
192.168.2.x. Machines A through F are on network 192.168.1.x. The machines X and Z are on network 192.168.2.x,
and machine G has access to both networks.
NIC A B C D E F G X Z
eth0 192.168.1.7 192.168.1.6 192.168.1.5 192.168.1.4 192.168.1.3 192.168.1.2 192.168.1.1 192.168.2.2 192.168.2.3
eth1 - - - - - - 192.168.2.1 - -
Using this port and addressing scheme, the networking system can pass data, addressing information, and type of
service information through the hardware, from one computer to another. The reason, there is an address for the
hardware card (ethernet address, also called MAC address), and another assigned address for that same card (IP
address), is to keep the parts of the network system that deal with the hardware and the software, independent of each
other. This is required in order to be able to configure the IP addressing dynamically. Otherwise, all computers would
have a static address and this would be very difficult to manage. Also, if a modification needs to be made to the
hardware addressing scheme for any reason, in ethernet, it will be transparent to the rest of the system. Conversely if a
TCP/IP Ports and Addresses
change is made to the software addressing scheme in the IP part of the system, the ethernet and TCP protocols will be
unaffected.
In the example above, machine F will send a telnet data packet to machine A. Roughly, the following steps occur.
1. The Telnet program in machine F prepares the data packet. This occurs in the application (Telnet),
presentation, and session layers of the OSI network model.
2. The TCP software adds a header with the port number, 23, to the packet. This occurs in the transport (TCP)
layer.
3. The IP software adds a header with the sender's and recipient's IP address, 192.168.1.2 to the packet. This
occurs in the network (IP) layer.
4. The ethernet header is added to the packet with the hardware address of the network card and the packet is
transmitted. This occurs in the link (Ethernet) layer.
5. Machine A's network card detects it's address in the packet, retrieves the data, and strips its header data and
sends it to the IP layer.
6. The IP layer looks at the IP header, and determines if the sender's IP address is acceptable to provide service to
(hosts.allow, hosts.deny, etc), and if so, strips the IP header and sends it to the TCP layer.
7. The TCP Layer reads the port number in it's header, determines if service is provided for that port, and what
application program is servicing that port. It strips the TCP header and passes the remainder of the data to the
telnet program on machine A.
Please note, that the network layers mentioned here are described in the next section. Also there are many types of
support at each of the four TCP/IP network system layers, but that issue is addressed in the next section.
Networking Tutorial NETWORK TOPOLOGY
0 komentar Ditulis oleh information technology education di 12.16Introduction
This guide is primarily about TCP/IP network protocols and ethernet network architectures, but also
briefly describes other protocol suites, network architectures, and other significant areas of networking.
This guide is written for all audiences, even those with little or no networking experience. It explains in
simple terms the way networks are put together, and how data packages are sent between networks and
subnets along with how data is routed to the internet. This document is broken into five main areas which
are:
1. Basics - Explains the protocols and how they work together
2. Media - Describes the cabling and various media used to send data between multiple points of a
network.
3. Architecture - Describes some popular network architectures. A network architecture refers to the
physical layout (topology) of a network along with the physical transmission media (Type of wire,
wireless, etc) and the data access method (OSI Layer 2). Includes ethernet, Token Ring, ARCnet,
AppleTalk, and FDDI. This main area of the document can and should be skipped by those
learning networking and read later.
4. Other Transport Protocols - Describes IPX/SPX, NetBEUI, and more.
5. Functions - Explains some of the functionality of networking such as routing, firewalls and DNS.
6. Further Details - Gives information about some protocols not covered in the "Basics" section. In
the future, it will include more information about packet fragmentation and re-assembly along
with more details about UDP and especially TCP and TCP connections.
7. More Complex functions - Documents multicasting, dynamic routing, and network management
8. Applications - Documents how some of the applications work such as ping and traceroute. In the
future, it will cover telnet, Rlogin, and FTP.
9. Other Concerns - Includes installing drivers, network operating systems, applications, wide area
networks, backing up the network and troubleshooting the network.
10. References - Includes a reference list of terms, RFCs and recommended reading.
The reader may read this document in any order, but for beginners, it would be best to read through from
the beginning with the exception of sections 2 (media), 3 (architecture), and 4 (other). At some point,
however, the reader should be able to break from the basics and read about routing and IP masquerading.
Introduction
There are no links to various reading material or software packages inside this document, except under
the references section. This is because it is more structured, and makes it easier to keep the document
current.
This document will first talk about the network basics so the reader can get a good grasp of networking
concepts. This should help the reader understand how each network protocol is used to perform
networking. The reader will be able to understand why each protocol is needed, how it is used, and what
other protocols it relies upon. This document explains the data encapsulation techniques in preparation
for transport along with some of the network protocols such as IP, TCP, UDP, ICMP, and IGMP. It
explains how ARP and RARP support networking. In functional areas, such as routers, several examples
are given so the user can get a grasp on how networking is done in their particular situation. This
document covers routing, IP masquerading, and firewalls and gives some explanation of how they work,
how they are set up, and how and why they are used. Firewalls and the available packages are described,
but how to set them up is left to other documentation specific to the operating system and the package.
Application protocols such as FTP and Telnet are also briefly described. Networking terms are also
explained and defined.
This document explains the setup of networking functions using Linux Redhat version 6.1 as an
operating system (OS) platform. This will apply to server functions such as routing and IP masquerading.
For more documentation on setting up packages, read documentation on this web site and other locations
specific to the operating system and the package. If you know how to set up other operating servers such
as Windows NT, you can apply the information in this document to help you understand how to
configure services on that OS platform.
This document was written because I perceived a need for a basic networking document to explain how
these networking services work and how to set them up, with examples. It will help a novice to learn
networking more quickly by explaining the big picture concerning how the system works together. I have
seen much good networking documentation, but little that explains the theory along with practical setup
and applications.
Network Topology
Network Topology
A network consists of multiple computers connected using some type of interface, each having one or more
interface devices such as a Network Interface Card (NIC) and/or a serial device for PPP networking. Each
computer is supported by network software that provides the server or client functionality. The hardware used to
transmit data across the network is called the media. It may include copper cable, fiber optic, or wireless
transmission. The standard cabling used for the purposes of this document is 10Base-T category 5 ethernet cable.
This is twisted copper cabling which appears at the surface to look similar to TV coaxial cable. It is terminated on
each end by a connector that looks much like a phone connector. Its maximum segment length is 100 meters.
Network Categories
There are two main types of network categories which are:
l Server based
l Peer-to-peer
In a server based network, there are computers set up to be primary providers of services such as file service or
mail service. The computers providing the service are are called servers and the computers that request and use
the service are called client computers.
In a peer-to-peer network, various computers on the network can act both as clients and servers. For instance,
many Microsoft Windows based computers will allow file and print sharing. These computers can act both as a
client and a server and are also referred to as peers. Many networks are combination peer-to-peer and server
based networks. The network operating system uses a network data protocol to communicate on the network to
other computers. The network operating system supports the applications on that computer. A Network Operating
System (NOS) includes Windows NT, Novell Netware, Linux, Unix and others.
Three Network Topologies
The network topology describes the method used to do the physical wiring of the network. The main ones are bus,
star, and ring.
1. Bus - Both ends of the network must be terminated with a terminator. A barrel connector can be used to
extend it.
2. Star - All devices revolve around a central hub, which is what controls the network communications, and
can communicate with other hubs. Range limits are about 100 meters from the hub.
3. Ring - Devices are connected from one to another, as in a ring. A data token is used to grant permission for
each computer to communicate.
There are also hybrid networks including a star-bus hybrid, star-ring network, and mesh networks with
connections between various computers on the network. Mesh networks ideally allow each computer to have a
direct connection to each of the other computers. The topology this documentation deals with most is star
topology since that is what ethernet networks use.
Web Programming with Continuations
1 The Big Idea
Scheme supports first-class continuations, which can be resumed an arbitrary
number of times. These continuations can be used to make HTTP behave
like a stateful protocol, and can even eliminate the need for session time-outs.
Although continuation-based approaches toWeb programming looks promising,
several important issues related to the use of continuations still need to
be addressed before these techniques will gain commercial acceptance.
2 The Problem
Since HTTP is a stateless protocol, Web applications themselves must maintain
conversational state with each client. The usual approach is to break the
application into a number of small pieces (JSP’s, Java Servlets, CGI scripts,
etc.), each of which is capable of handling a small number of requests.
This approach suffers from several problems:
• legacy applications not written in this style are difficult to adapt to the
Web
• breaking the application into pieces may make it harder to modify the
application
• screen flow is difficult to handle in general, as users can clone the
browser window, submit simultaneous requests, bookmark pages, or
hit the ”Back” button on the browser
• techiques to maintain state often require each piece of the Web app to
manipulate objects in a ”session” hash table, resulting in side-effects
and dependencies that can cause subtle bugs
3 USING CONTINUATIONS TO ADD STATE TO THE WEB 3
3 Using Continuations to Add State to the
Web
Since a continuation is a first-class value in Scheme and can be invoked an
arbitrary number of times, continuations can be used to add state to a Web
application. Whenever the Web application needs input from the user, the
app saves the current continuation associated with that user. When the user
responds with some information, the saved continuation is restored, and the
input provided by the user is returned as the value of the continuation.
Since a continuation can be invoked multiple times, a user can bookmark
a page and return to the page later. As long as the continuation still exists,
the user can begin interacting with the application at that point in the
”conversation”.
For example, imagine someone who frequently uses an airline reservation
site to fly the same route each week. The site might require that the route
information be entered by the user each time a flight is booked. To save
time, the user may wish to fill in the information once, then bookmark the
next page of the transaction. As long as the continuation saved at that point
is still valid, the user can go back to the site in the future and book a new
flight without having to enter the route information again.
Note that in this case the user is able to save a pending transaction at an
arbitrary point not explicitly supported by the designers of the Web site.
4 Issues to Consider
You will need to consider the following issues before using continuations in
your Web application:
4.1 Saving the continuation
There are three basic approaches to saving continuations: save them on the
server, on the client, or make the decision at run-time.
4.1.1 Save it on the Server
This approach reduces bandwidth, but has implications with respect to storage
space and session timeouts. The saved continuation is usually mapped
4 ISSUES TO CONSIDER 4
to a unique URL by which it is invoked.
4.1.2 Save it on the Client
Once again, there are a couple of options here. The general tradeoff is that
you reduce storage requirements on the server at the expense of increased
bandwidth. In addition, you must be able to serialize/unserialize your continuation
in some way.
1. Save the continuation in a cookie
The advantage is that the continuation is persistent, eliminating session
timeouts. A disadvantage is that you must deal with the submittal of
older versions of continuations. Also, most browsers limit the size of
cookies to a few kilobytes.
2. Save the continuation in a hidden field
This may be the only option for saving larger continuations on the
client-side. Session timeouts are still a problem.
4.1.3 Hybrid Approach
Look at the size of each continuation before deciding where to save the continuation.
This approach combines some of the benefits of the previous two
approaches, at the expense of additional complexity.
4.2 Simulating Continuations in Other Languages
Even if you are programming in a language that doesn’t have explicit continuation
support, there are still ways to use some of these techniques. See
”Automatically Restructuring Programs for theWeb” (Graunke, et al., 2002)
for details on CPS, lambda lifting and defunctionalization.
Continuations can be simulated in Java by using exception handling, as
is done in the Kawa Scheme interpreter. Unfortunately, these fake continuations
are strictly less powerful than the real thing, and cannot be used to
simulate co-routines, for example. For details, see
http://www.delorie.com/gnu/docs/kawa/kawa-tour 19.html
5 ADVANTAGES 5
5 Advantages
Using continuations to add conversational state to a Web application has
numerous advantages over traditional mechanisms:
• Can structure the program to match the problem.
• Gracefully handles unusual navigational patterns.
• Can use standard development tools, including debuggers.
• Can port legacy software to the Web more readily.
• Provides for a more rigorous understanding of program structure and
Web navigation.
• Can store conversational state on the client’s browser, if desired.
• Can take advantage of standard automatic program transformations.
6 Limitations
Unfortunately, all is not sunshine when using continuations in your Web app.
Here are a few real disadvantages of a continuation-based approach:
• Continuations seem to be hard to understand.
• What if your language doesn’t support first-class continuations?
• Where do you save the continuation?
• Garbage collection:
– How long before you empty the trash?
– How to handle distributed garbage collection?
• Must a continuation be associated with a unique thread?
• How do you reconcile continuations with persistent stores?
• How do you manage software versioning with continuations?
7 SOME SYSTEMS IN USE 6
• If you use CPS, will anyone be able to understand your code?
• Will ease of implementation drive the user experience?
• Are continuations efficient?
• How do you convince your boss that this approach works?
7 Some Systems in Use
Here are a few Web-based systems that use either continuations or CPS to
help maintain state:
Yahoo! Store http://store.yahoo.com/ (formerly ViaWeb)
See http://www.paulgraham.com/lib/paulgraham/bbnexcerpts.txt for
details.
Persistent Server-Side Scheme Interpreter (PS3I)
(http://youpou.lip6.fr/queinnec/VideoC/ps3i.html)
See the papers by Christian Queinnec in the Further Reading section
of this paper for more information on PS3I and the Universit´e Paris
CD-ROM.
Universit´e Paris CD-ROM (http://videoc.lip6.fr/)
HTDP Web Server (http://www.htdp.org)
See the papers by Paul Graunke, et al., for details.
Other Systems See the comp.lang.scheme thread I started on November
19, 2002.
8 Open Problems
As I see it, the three biggest technical hurdles preventing adoption of continuationbased
Web programming in the commercial sector are:
1. dealing with side effects, especially mutable stores
9 A MODEST PROPOSAL 7
2. determining the best manner in which to save continuations
3. designing systems so that the GUI does not receive sloppy seconds
Graham may have solved some or all of these problems in designing ViaWeb
- I’ll ask him.
9 A Modest Proposal
If the Metro-Schemers group decides to create a Web site, I propose that we
use a continuation-based architecture. This would better allow us to see how
a continuation-based system works in practice.
One possibility might be to use the DrScheme TeachPack mentioned
in ”Automatically Restructuring Programs for the Web” (Graunke, et al.,
2002).
10 Further Reading
Perhaps the best source for in-depth information about Scheme is Jim Bender’s
”Bibliography of Scheme-related Research” at http://library.readscheme.org/
Most relevant to this presentation is Bender’s ”Reading list on XML and
Web Programming” at http://readscheme.org/xml-web/ and his ”Continuations
and Continuation Passing Style” page at http://library.readscheme.org/page6.html.
Unless indicated otherwise, links to all of these papers are available on
Jim’s site.
10.1 Continuations
The following books and papers contain much useful information on continuations:
• R. Kent Dybvig. The Scheme Programming Language (2nd ed.). Prentice
Hall, 1996.
Entire text available online at http://www.scheme.com/tspl2d/index.html.
Sections 3.3 and 3.4 introduce continuations and continuation-passing
style, respectively.
10 FURTHER READING 8
• Paul Graham. On Lisp. Prentice Hall, 1993.
Entire text available online at http://www.paulgraham.com/onlisptext.html.
Chapter 20 contains an in-depth examination of Scheme continuations.
• Robert Hieb, R. Kent Dybvig, and Carl Bruggeman. ”Representing
Control in the Presence of First-Class Continuations”. ACM SIGPLAN
1990 Conference on Programming Language Design and Implementation.
June 1990.
This paper examines how to efficiently implement continuations, which
may provide the reader with additional insight into the nature of continuations.
• John Small. ”Introducing PLT Scheme.” Pea Pod Publishing (Rogare
L.L.C.), Great Falls, Virginia, 2002.
Available at http://www.rogare.com/metro-schemers/intropltscheme.pdf.
Chapter 3 contains an in-depth look at continuations.
10.2 Web Programming with Continuations
These documents show how continuations and continuation-passing style can
be useful in Web application development:
• Paul Graham. ”Lisp in Web-Based Applications”. Excerpt of talk
given at BBN Labs in Cambridge, MA, April 2001.
Available at http://www.paulgraham.com/lib/paulgraham/bbnexcerpts.txt
Graham briefly explains how the architecture of ViaWeb exploited
continuation-passing style.
• Paul Graunke, Robert Findler, Shriram Krishnamurthi, Matthias Felleisen.
”Automatically Restructuring Programs for the Web”. Automated
Software Engineering 2001. 2001.
This paper explains how to use several automatic program transformations
(including CPS) to allow Web-based programs to be written in a
simpler fashion than usual.
10 FURTHER READING 9
• Paul Graunke, Shriram Krishnamurthi, Van der Hoeven and Matthias
Felleisen. ”Programming the Web with High-Level Programming Languages”.
Proceedings of ESOP 2001. 2001.
Explains how features of a high-level programming language, including
first-class continuations, allow for simple yet efficient creation of Web
applications.
Membuat Yahoo multi messenger lewat regedit kita
0 komentar Ditulis oleh information technology education di 19.55Ini merupakan suatu hal yang sebenarnya sudah lama beredar di dunia maya, bagaimana sih membuat yahoo multi messenger lewat regedit kita, dari hasil penelusuran hasil browsing lewat dunia internet, dan dari situs situs forum internet. disini kita akan mencoba membuatnya.
Bagaimana ya klo kita kepingin online di yahoo messenger lebih dari satu pada satu pc.
nah inilah caranya menurut bang bombom winarno, hehehe?
1. pastikan program yahoomessenger udah terinstal
2. edit regedit saudara masuk menu run tulis regedit
3. masuk ke file HKEY_CURRENT_USER masuk file SOFTWARE masuk file YAHOO masuk file PAGER masuk file TEST.
disini akan terlihat satu file nama file (Default) Type REG_SZ tipe data (value not set).
4.disitu tambahkan file dngan cara klick kanan pilih REG_DWORD beri nama file tersebut dengan nama Plural dan massukkan value data=1 pilih hexadesimal.
5. safe file tersebut.
6. reboot komputer dan setelah itu coba jalankan yahoo kamu lebih dari satu, semoga berhasil.
Solusi Sharing file xp dengan vista bermasalah
0 komentar Ditulis oleh information technology education di 14.20Bagaimana kita Sharing File apabila dalam system operasi windows Vista Bermasalah, Disini akan sedikit dulas bagaimana cara windows xp dengan vista bisa saling bertukar informasi dan berkomuniasi,
Langkah- langkah men nonaktifkan NTLMv2 :
- Disable UAC
- jalankan perintah "Run" dengan cara menekan tombol Windows+R di desktop
-ketik "msconfig", enter
-pilih tab "tools"
-scroll ke bawah sampe ketemu "Disable UAC", pilih dan klik "Launch"
-akan muncul layar command prompt, sekarang sudah mati nion-68:
-exit, dan klik ok. Restart komputer.
- Matikan NTLMv2
- kalo sudah disable UAC (kalo tidak mematikan bisa denganc ara ini), sekarang kita matiin NTLMv2:
-jalankan perintah "Run" dengan cara menekan tombol Windows+R di desktop
-ketik "secpol.msc", enter
-klik "Local Policies"
-klik "Security Options"
-scroll ke bawah, cari "Network Security: LAN Manager Authentication Level", klik kanan, pilih "Properties"
-dari scroll box, pilih "Send LM & NTLM - Use NTLMv2 session security if negotiated", klik ok
3. OPTIONAL
mumpung sudah di layar security options, kalo mau bisa sekalian matiin feature yang cukup menggangu dari Vista: untuk koneksi file sharing antara
-masih di "Security Options"
-pilih "Network Access: Let Everyone Permissions Apply to Anonymous Users" --> set ke "Enable"
-pilih "Network Access: Restrict Anonymous Access to Named Pipes and Shares" --> set ke "Disable"
-nah, beres sudah. Somoga berhasil, dan membantu Teman Teman…
For English : how do we sharing when in system windows operation vista vb4, here a little dulas how does windows manner xp with vista mutual can swop information and communication, there cause that causes windows system vista can not share: system kemamanan network ntlmv2 exist in vista.
steps men deactivate ntlmv2:
1. menyable uac
- run command" run" by button windows+r at desktop
-ketik" msconfig" , enter
-pilih tab" tools"
-scroll downwards sampe meet" menyable uac" , choose and click" launch"
-a appear sail command prompt, now die nion-68:
-exit, and click ok. restart computer.
2. kill ntlmv2
- kalo menyable uac (kalo not lethal denganc this fig), now we matiin ntlmv2:
-jalan command" run" by button windows+r at desktop
-ketik" secpol. msc" , enter
-klik" local policies"
-klik" security options"
-scroll downwards, look for" network security: lan manager authentication level" , click right, choose" properties"
-dari scroll box, choose" send lm ntlm - use ntlmv2 session security if negotiated" , click ok
3. optional
as long as at sail security options, kalo want can all matiin feature enough harry from vista: for file connection sharing between vista with os other, he always ask computer has username and password. sebener also less ngerti manner ngeset his password. so, kill aja, let guest and whoever can access to file that i share (besides we can ngeset so that file whom we share only" read-only" , so not problem). the lethal manner:
-masih at" security options"
-pilih" network access: let everyone permissions apply to anonymous users" --> set to" enable"
-pilih" network access: restrict anonymous access to named pipette and shares" --> set to" menyable"
-nah, neat. somoga success, and help friends
Tricks Mendapatkan Money Dollar dari Google AdSense Secara Cuma-Cuma
0 komentar Ditulis oleh information technology education di 13.16
CARA MENDAFTAR GOOGLE ADSENSE (GRATIS):
Bila ingin situs Anda diterima (lulus review) oleh Google, ikuti langkah-langkah pendaftaran sebagai berikut:
- Miliki Email GMAIL.COM - xyz@gmail.com (WebMail nya Google). Bila Anda belum punya, kami bisa bantu.
- Max. 2 hari kerja, cek Email Anda dan cari undangan dari Google. Klik link pada isi pesan undangan tersebut. - Setelah Anda memiliki Email apasaja@gmail.com, langkah selanjutnya buat Blog (situs pribadi) dialamat http://www.blogger.com (Klik link "New Blogger" - ketik Username & Password sama dengan Username & Password account GMAIL.COM Anda)
- Mulailah untuk membuat Blog Anda (carilah topik yang Anda sukai, misalnya tentang hobi Anda, peluang usaha yang Anda miliki, dsb). Saran kami, siapkan paling sedikit 4 artikel dan HARUS DALAM BAHASA INGGRIS. Bila ingin mudah, gunakan software penterjemah (seperti TransTool - Anda bisa mengetik dalam bahasa Indonesia dan program akan langsung mengubahnya dalam bahasa Inggris). Kirimkan artikel ini ke Blog Anda (jangan lupa untuk memberi judul yang menarik). Anda bisa dapatkan software penterjemah di Mal Ambasador Kuningan atau toko software terkemuka di daerah Anda.
- Pasang 2-3 video dari YouTube.com di Blog Anda (optional)
- Setelah Blog Anda siap (memiliki sedikitnya 4 artikel), sekarang Anda telah siap untuk melakukan langkah terakhir YANG PALING PENTING yaitu mendaftar ke Google AdSense. Proses pemeriksaan memakan waktu 3-5 hari kerja. Untuk mendaftar, silakan klik link Banner dibawah ini...Kami sarankan untuk banyak berdoa agar situs Anda lulus diperiksa oleh Mbah Google :-
manner sign-ups google adsense (free) with how get money dollar according to gratis:
when want your site accepted (to pass review) by google, follow enrollment steps as follows:
1. has email gmail. com - xyz@gmail. com (webmail he google). when do you not yet has, we can help.
- max. 2 workday, your email cheque and look for invitation from google. click link in invitation message contents.
2. after you have email apasaja@gmail. com, step furthermore make blog (individual site) mengalamat http: /www. blogger. com (click link" new blogger" - type username password equal to username password account gmail. com you)
3. begin to make blog you (look for topic whom you take a fancy to, for example about your hobby, effort opportunity whom you have, etc). our suggestion, prepare most a little 4 articles and must in english. when want easy, use software translator (to like transtool - you can type in indonesian and program direct change it in english language). send this article to blog you (don't forgets to give title that interesting). you can get software translator at mal ambasador brass or foremost software store at your region.
4. pair 2-3 video from youtube. com at blog you (optional)
5. after blog you ready (has at least 4 article)s, now you ready for have done latest step importantest that is has sign-upped to google adsense. investigation process consumes time 3-5 workday. to sign-up, please click link banner under this. . . we suggest to many pray so that your site passes to inspected by mbah google: -)
achieve many profits here, with get money according to free from google adsense
WEB LECTURE
WEB KAMPUS
Style Baju Muslim Murah
-
New September 2012 - [image: Rp150.000,00] DSC 1010 Rp145.000,00 [image: Rp145.000,00] DSC 1011 Rp145.000,00 DSC 1015 Rp150.000,00 DSC 1017 Rp150....11 tahun yang lalu
CV. LUANTJAR DJAJA
Luantjar Djaja
Perusahaan Luantjar Djaja didirikan pada tanggal…tahun 2004 sesuai akte pendirian no….Luantjar Dajaja berbentuk sebuah CV (perusahaan komanditer) yang bertempat di Delta sari indah no. 104 Waru-Sidoarjo. Pada tahap awal perusahaan ini masih digolongkan sebagai industri kecil menengah yang nantinya kami optimis akan menjadi sebuah perusahaan yang besar dan bersaing dengan perusahaan lainnya yang sejenis.
Kegiatan perusahaan kami bergerak di bidang jasa IT (Information Technology) baik sebagai konsultan maupun yang lainnya. Memang kami sadar bahwa perusahaan kami masih baru akan tetapi untuk kemampuan kami cukup bersaing.
Perusahaan kami cukup andal dalam hal tenaga kerja, ini dikarenakan semua tenaga kerja kami lulusan dari sebuah perguruan tinggi negeri yang berkompeten dalam IT.
Sehubungan dengan kebijakan pemerintah Indonesia menuju Indonesia Go Open Source (IGOS) dan penegakan UU HaKI (hak kekayaan intelektual) tentang pembajakan perangkat lunak yang masih merajalela di bumi Indonesia.
Linux Education Centre
Contac Person :
Adhytiya Handoko :
31-7885404,0856-3473261
Hormat kami
Directur Marketing Directur
Adhytia Handoko,A.Md M. & Syariefuddien Z, S.Pd.,M.T